Anura Fernando, Chief Innovation Architect for Medical Systems Interoperability & Security, Underwriters Laboratories (UL)12.10.18
Today, most people in the world communicate using electronic devices and the majority have at least heard the word “cybersecurity.” However, how many people really understand what cybersecurity is? The security pundits and purists might argue about technical distinctions, using terms like “information security” or “cyber physical systems’ security,” or any of a dozen other related terms; but ultimately, whatever this problem is, most of the world thinks about one thing when they hear the term: “Could I be hacked?” In order to answer this question, the term cybersecurity needs to be well understood, and this will help us all improve the cybersecurity posture of the technologies we deal with every day, whether it’s the cell phones through which we communicate, the medical devices we use at home, or the products we design. So, let’s take a deeper dive together to see what cybersecurity really entails, and you won’t need to be a “hacker” or a security engineer to understand it.
A System-Level Definition
Cybersecurity is a facet of a multidisciplinary “systems” problem. Some say that it is just a subset of software quality requirements, but we will see that it is really an aspect of complete system-level quality management. Why? Simply because “software” by itself cannot do anything. It merely exists until it is installed on a hardware platform that allows it to interact with the world.
Just 15 to 20 years ago, many consumer product development companies had separate “hardware” teams and “software” teams, even for the development of electronic controls. When control system problems arose in the field, fingers would start pointing in both directions. “Systems Engineering” was a relatively new discipline, at least within the consumer product space, and most systems engineering at that time was practiced in the defense, aerospace, and transportation sectors. Today, most electrical engineers leave school with quite a bit of software training, and many computer scientists leave school having built some type of hardware on which their software can operate.
Understanding Cybersecurity In ‘Sociotechnical’ Terms
So, if we are now developing a more capable, multidisciplinary workforce than we’ve had in the recent past, why are we still encountering all these cybersecurity problems? The core answer to this question is that cybersecurity is not just a technical problem, but rather a “sociotechnical” problem. To better understand this, we will look to try to understand more about the opposite of cybersecurity, which is “interoperability.”
Interoperability is basically the ability of things to interact with each other in established ways. In cybersecurity, we are often generally trying to prevent things from being accessed or acted upon by others. However, doing so in an exclusive way would significantly limit the potential benefits to be gained from intercommunication. Would you have a television in your home if it were fully secure from any incoming signals? Likely not. Therefore, product designers often must think carefully about what interactions are needed and then design mechanisms by which certain other authenticated products or people (i.e., those deemed to be acceptable members of the ecosystem) can be authorized (i.e., given permission) to interact with the product that the product designer is responsible for developing. This formation of ecosystems of interoperable products has been modeled in a variety of ways, but a particularly useful model for this discussion is that of the Coalition Interoperability model, developed by Andreas Tolk as shown in the graphic1.
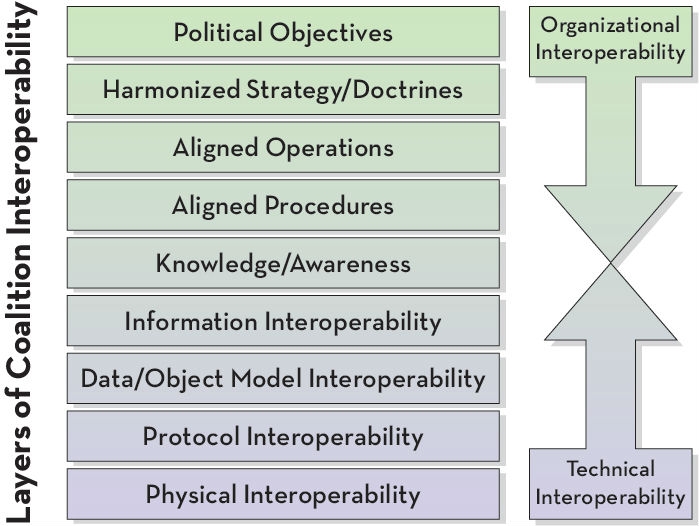
Coalition Interoperability (Tolk)1
In the graphic, we see that for technologies to be “interoperable” there are many layers of interaction that must be carefully managed. In theory, all of these interdependencies could be perfectly aligned, and information flow could be perfectly controlled through authentication and authorization mechanisms, but unfortunately, as we all know, we don’t live in a perfect world. It is the “real world” mismatches in the alignment of these layers and the imperfections in authentication and authorization processes that create the cybersecurity phenomena known as “vulnerabilities.”
Cyber Vulnerabilities in Healthcare
We can look at how this might affect our critical national infrastructure through an examination of the healthcare supply chain. Hospitals have the overarching political objective of providing the best possible affordable care to patients. Many hospitals have recognized that security vulnerabilities in hospital infrastructure, including medical devices, could compromise the safety of their patients. They have therefore developed strategies and doctrine for mitigating these vulnerabilities. However, there are still many hospitals that have not taken such measures. It is important to recognize this fact in the context that it is increasingly becoming a necessity for patient data to be captured in electronic health records (EHRs), often from mobile medical devices or even home healthcare products. This trend is occurring both for purposes of reducing healthcare costs as well as improving care by giving patients faster and more direct access to their own health information. This can also help patients play a more proactive role in the management of their own care, often from the comfort of their own homes.
When we look at the graphic in this context, we can ask ourselves some questions:
In all these situations, it is important to understand the fine balance between convenience, care, security, and the many different views of patient privacy that may be jurisdiction dependent.
Managing Cyber Vulnerabilities
So now that we understand the word “cybersecurity” a little better, we can see what tools are available to help us better manage these inevitable vulnerabilities. First and foremost is the Cyber Security Framework (CSF) from the National Institute of Standards and Technology (NIST). This framework serves as the foundation for many of the current best practices and standards. The NIST CSF has served as the foundation for the development of standards such as UL 2900-2-1, Software Cybersecurity for Network-Connectable Products, Part 2-1: Particular Requirements for Network Connectable Components of Healthcare and Wellness Systems. As an FDA Recognized Consensus Standard, this standard applies to both organizational process requirements and technical product requirements aligning medical device capabilities with the needs of system integrators such as hospitals. The use of such standardized requirements in the procurement process helps to better align interests and minimize the kinds of mismatches that we saw when examining the Coalition Interoperability model.
So, now that we understand what “cybersecurity” is, perhaps at least a little bit more, let’s use that knowledge to better protect our critical healthcare infrastructure.
Reference
1 Information from Figure 3 from System of Systems Interoperability (SOSI): Final Report https://pdfs.semanticscholar.org/d649/3a57552eda7031283d5e660f6d3ad9923326.pdf?_ga=2.59466090.614929910.1544472172-1979073409.1544472172
A System-Level Definition
Cybersecurity is a facet of a multidisciplinary “systems” problem. Some say that it is just a subset of software quality requirements, but we will see that it is really an aspect of complete system-level quality management. Why? Simply because “software” by itself cannot do anything. It merely exists until it is installed on a hardware platform that allows it to interact with the world.
Just 15 to 20 years ago, many consumer product development companies had separate “hardware” teams and “software” teams, even for the development of electronic controls. When control system problems arose in the field, fingers would start pointing in both directions. “Systems Engineering” was a relatively new discipline, at least within the consumer product space, and most systems engineering at that time was practiced in the defense, aerospace, and transportation sectors. Today, most electrical engineers leave school with quite a bit of software training, and many computer scientists leave school having built some type of hardware on which their software can operate.
Understanding Cybersecurity In ‘Sociotechnical’ Terms
So, if we are now developing a more capable, multidisciplinary workforce than we’ve had in the recent past, why are we still encountering all these cybersecurity problems? The core answer to this question is that cybersecurity is not just a technical problem, but rather a “sociotechnical” problem. To better understand this, we will look to try to understand more about the opposite of cybersecurity, which is “interoperability.”
Interoperability is basically the ability of things to interact with each other in established ways. In cybersecurity, we are often generally trying to prevent things from being accessed or acted upon by others. However, doing so in an exclusive way would significantly limit the potential benefits to be gained from intercommunication. Would you have a television in your home if it were fully secure from any incoming signals? Likely not. Therefore, product designers often must think carefully about what interactions are needed and then design mechanisms by which certain other authenticated products or people (i.e., those deemed to be acceptable members of the ecosystem) can be authorized (i.e., given permission) to interact with the product that the product designer is responsible for developing. This formation of ecosystems of interoperable products has been modeled in a variety of ways, but a particularly useful model for this discussion is that of the Coalition Interoperability model, developed by Andreas Tolk as shown in the graphic1.

Coalition Interoperability (Tolk)1
In the graphic, we see that for technologies to be “interoperable” there are many layers of interaction that must be carefully managed. In theory, all of these interdependencies could be perfectly aligned, and information flow could be perfectly controlled through authentication and authorization mechanisms, but unfortunately, as we all know, we don’t live in a perfect world. It is the “real world” mismatches in the alignment of these layers and the imperfections in authentication and authorization processes that create the cybersecurity phenomena known as “vulnerabilities.”
Cyber Vulnerabilities in Healthcare
We can look at how this might affect our critical national infrastructure through an examination of the healthcare supply chain. Hospitals have the overarching political objective of providing the best possible affordable care to patients. Many hospitals have recognized that security vulnerabilities in hospital infrastructure, including medical devices, could compromise the safety of their patients. They have therefore developed strategies and doctrine for mitigating these vulnerabilities. However, there are still many hospitals that have not taken such measures. It is important to recognize this fact in the context that it is increasingly becoming a necessity for patient data to be captured in electronic health records (EHRs), often from mobile medical devices or even home healthcare products. This trend is occurring both for purposes of reducing healthcare costs as well as improving care by giving patients faster and more direct access to their own health information. This can also help patients play a more proactive role in the management of their own care, often from the comfort of their own homes.
When we look at the graphic in this context, we can ask ourselves some questions:
- What happens when one network-connected device is replaced by another during the patient care regimen?
- What happens when a patient’s care shifts from one department in the hospital to another?
- What happens when a patient is transferred from one hospital to another in the same hospital network?
- What happens if the patient is sent home with a monitoring device?
- What happens when a patient moves to another hospital network or to another state?
- What happens when a patient moves to another country?
In all these situations, it is important to understand the fine balance between convenience, care, security, and the many different views of patient privacy that may be jurisdiction dependent.
Managing Cyber Vulnerabilities
So now that we understand the word “cybersecurity” a little better, we can see what tools are available to help us better manage these inevitable vulnerabilities. First and foremost is the Cyber Security Framework (CSF) from the National Institute of Standards and Technology (NIST). This framework serves as the foundation for many of the current best practices and standards. The NIST CSF has served as the foundation for the development of standards such as UL 2900-2-1, Software Cybersecurity for Network-Connectable Products, Part 2-1: Particular Requirements for Network Connectable Components of Healthcare and Wellness Systems. As an FDA Recognized Consensus Standard, this standard applies to both organizational process requirements and technical product requirements aligning medical device capabilities with the needs of system integrators such as hospitals. The use of such standardized requirements in the procurement process helps to better align interests and minimize the kinds of mismatches that we saw when examining the Coalition Interoperability model.
So, now that we understand what “cybersecurity” is, perhaps at least a little bit more, let’s use that knowledge to better protect our critical healthcare infrastructure.
Reference
1 Information from Figure 3 from System of Systems Interoperability (SOSI): Final Report https://pdfs.semanticscholar.org/d649/3a57552eda7031283d5e660f6d3ad9923326.pdf?_ga=2.59466090.614929910.1544472172-1979073409.1544472172